You won’t find an icon for it or a shortcut in your launcher, yet it’s one of the most connected pieces of Samsung’s software. com.samsung.android.mdecservice is the background engine behind Call & Text on Other Devices, the feature that lets your Galaxy phone and tablet share calls, texts, and notifications in real time. The package name may look cryptic, but this service is what makes the Samsung ecosystem feel continuous — the reason your tablet rings when your phone is in another room.
What com.samsung.android.mdecservice Actually Does
The Multi-Device Experience Connector Service (MDEC) acts as a silent bridge between every Samsung device signed into the same Samsung Account. When a call arrives, it listens through the phone’s telephony framework, mirrors the event over Wi-Fi Direct or Bluetooth LE, and recreates the ring and caller ID on your linked tablet or watch. Text messages follow the same path. Everything runs under encrypted sockets authenticated by your Samsung Account credentials, so the data never travels through public cloud APIs.
It first appeared in Android 9 with One UI 1.0 as a small, 5 MB helper app. In One UI 7, the same connector has grown into a 22 MB system module targeting Android 15 (API 35). The latest verified build, 8.0.00.15, is signed with Samsung’s official RSA key and compiled with no debug or backup flags — the digital fingerprint of a production system component.
Why It Exists
Samsung built MDEC to extend the idea of continuity that Apple had perfected with its ecosystem. Instead of forcing you to switch devices, it lets your calls, messages, and app notifications roam seamlessly. The service sits beneath visible apps like Call & Text on Other Devices and SmartThings, managing device discovery, authentication, and message routing.
When your tablet is idle, MDEC keeps a lightweight listener alive through Firebase Messaging. Once a call event arrives, it wakes the device, opens an encrypted socket, and transmits only metadata — not audio — to start the relay. Audio is streamed peer-to-peer through Wi-Fi Direct.
When the feature is disabled, all listeners sleep. That design explains why the process reappears after every reboot: it’s marked as persistent with the RECEIVE_BOOT_COMPLETED permission.
Is It Safe or Spyware?
Despite the scary permission list, it’s safe. Our static analyzer confirms a clean Samsung signature (SHA-256 = 7572e7b5ea4b33d60b5acd90ee95f329267e5213452cc1a0a35b9c10decd3621) with JAR v1 signing and no test or debug traces.
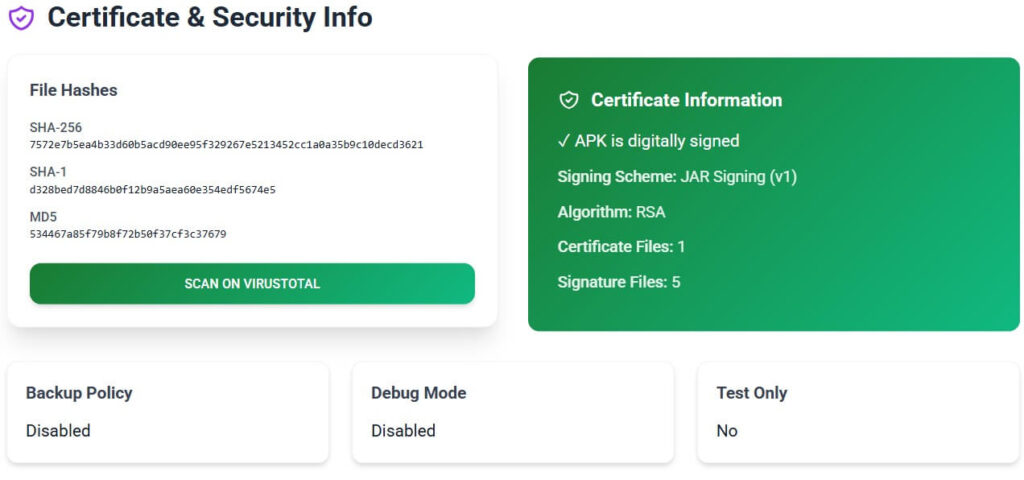
Security scanners occasionally flag it because of patterns common to remote-communication apps: reading SMS, contacts, and call logs, starting at boot, and maintaining sockets in the background. Those behaviors trigger YARA privacy-risk rules but are required for mirroring calls and texts. The app contains no third-party ad or tracking SDKs. Only three frameworks were detected: Firebase (analytics), AndroidX, and Kotlin runtime — all standard.
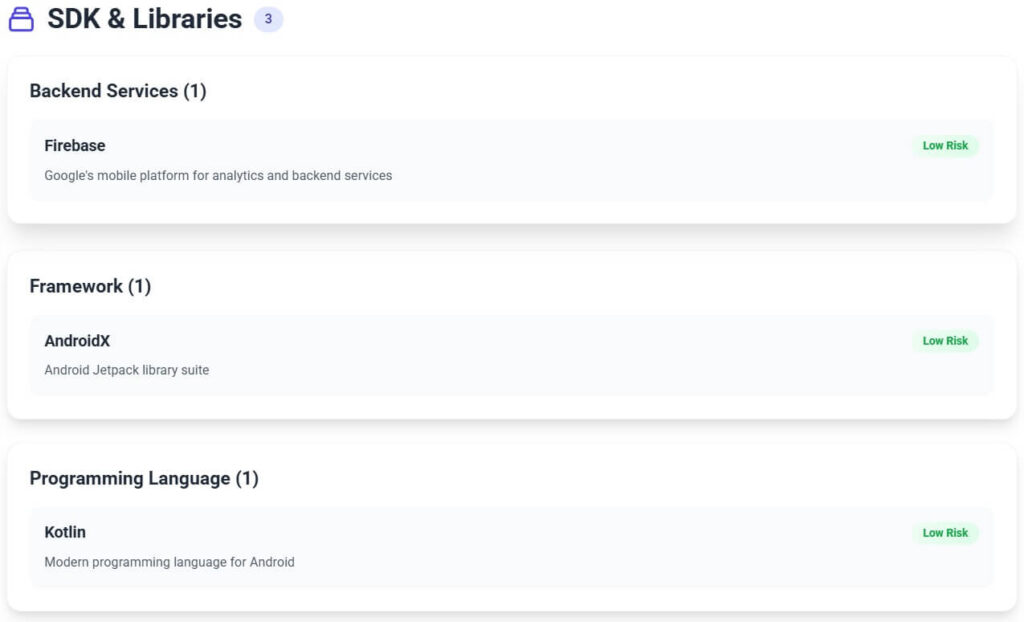
In short, it’s powerful, not invasive.
Why It Keeps Running
MDEC never fully sleeps because it’s responsible for maintaining the link between devices. It registers broadcast receivers for boot, package changes, SIM events, and connectivity updates. Android treats it as a foreground-capable system service, meaning the OS will restart it if terminated. That’s why it occasionally appears high in battery statistics even when unused.
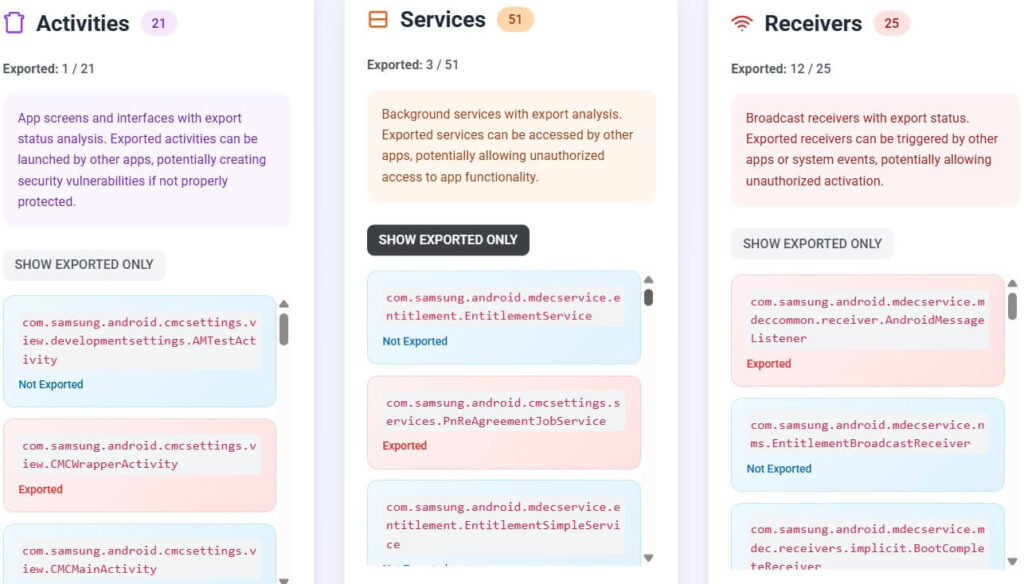
Its footprint — 51 services and 25 receivers, with just 3 exported — might sound heavy, but most components stay dormant until a companion device connects. Each exported element is guarded by Samsung-specific permissions such as com.samsung.android.mdecservice.DYNAMIC_RECEIVER_NOT_EXPORTED_PERMISSION, which block third-party access. What looks like constant activity is often only network listening or FCM token refresh, measured in kilobytes per day.
Why You Can’t Uninstall or Disable It
com.samsung.android.mdecservice lives under the shared UID android.uid.system, meaning it’s part of the signed system image. Android’s package manager prevents user-level uninstallation, and even disabling it through package-disabler apps can cause dependency errors in Samsung Messaging, SmartThings, and Samsung Account.
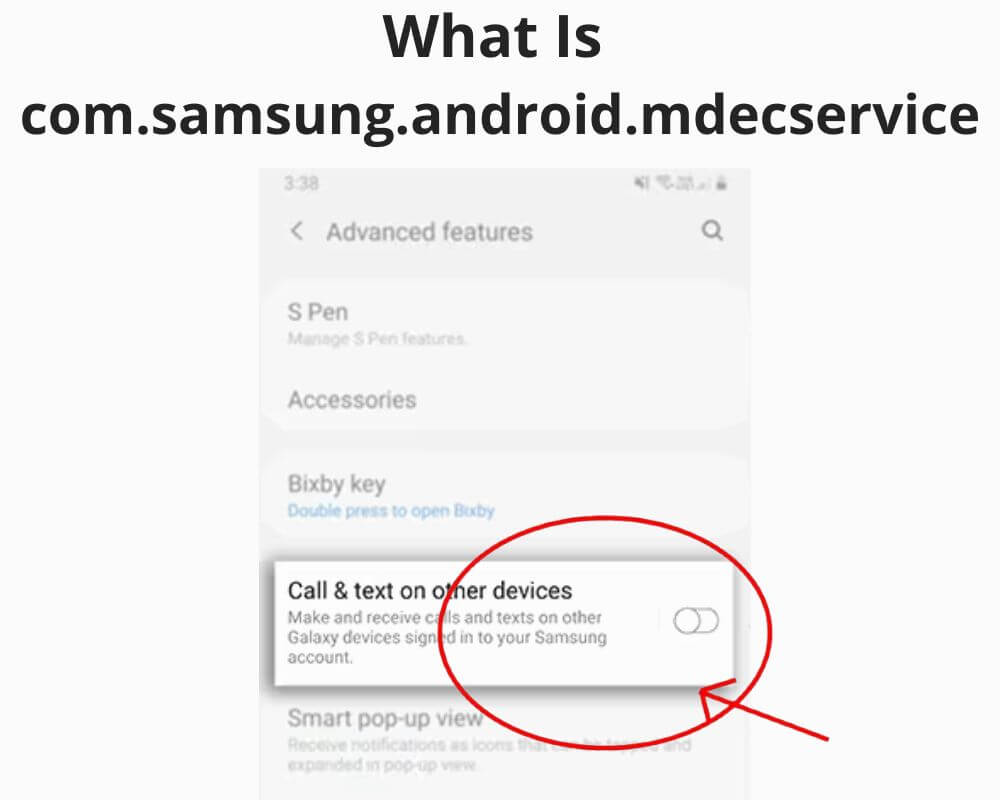
The safe method to turn it off is through the public switch:
Settings › Advanced features › Call & Text on Other Devices › Off.
That command halts the connectors, unregisters receivers, and releases background sockets without altering system integrity. Deleting the APK isn’t recommended; it will simply re-install with the next firmware update.
When “com.samsung.android.mdecservice Has Stopped” Appears
This crash message surfaces after major updates or when device linking fails. The cause is straightforward: cached data from an old version collides with new entitlement rules or outdated tokens. The fixes are safe and simple:
- Clear cache and data: Go to Settings › Apps › Call & Text on Other Devices › Storage and tap Clear cache then Clear data.
- Re-link your devices: Turn the feature off, reboot both phone and tablet, then enable it again.
- Update the companion app: Open the Galaxy Store and install the latest 8.0.00.15 release or newer.
- Re-add your Samsung Account: Removing and re-signing restores authentication tokens.
Force-stopping rarely helps because Android restarts the service automatically. Once cache and account data are refreshed, the crashes disappear.
Permissions in Context
The manifest declares 48 permissions — five marked dangerous and two signature-level. These include READ_SMS, SEND_SMS, READ_CONTACTS, READ_CALL_LOG, WRITE_CALL_LOG, and MODIFY_PHONE_STATE. Their presence can look alarming, but each maps directly to a user-visible action: syncing messages, updating missed-call lists, and controlling telephony state during relayed calls.
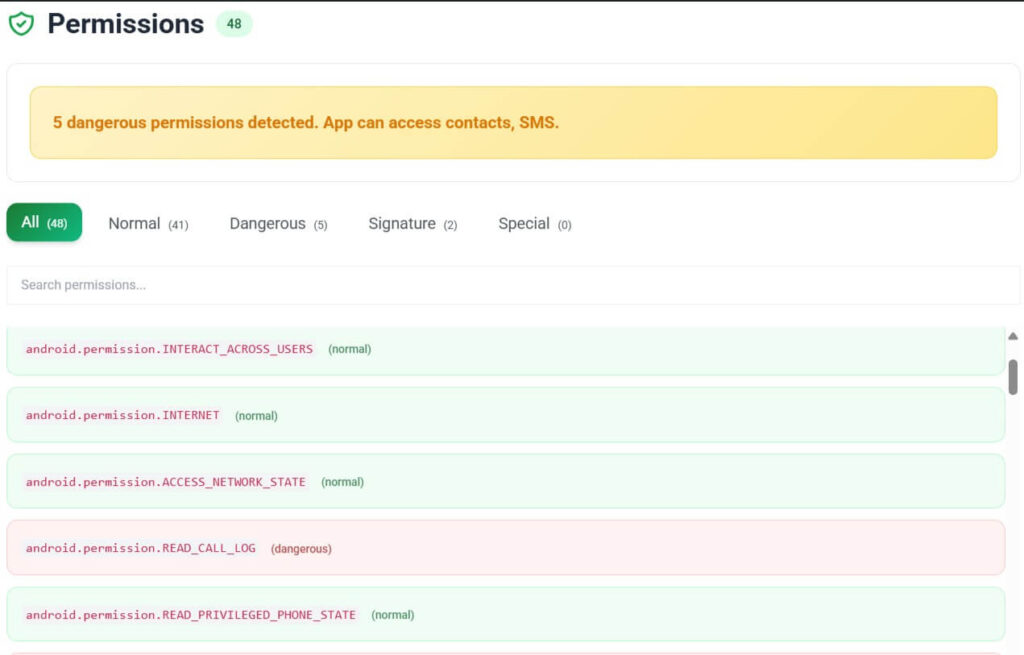
Every dangerous permission is sandboxed within Samsung’s system UID and inaccessible to other apps. No exported content providers or unsecured intents exist. The architecture favors reliability over minimalism: one process handles SMS sync, another manages VoIP relay, and a third coordinates push notifications through Firebase. Together they maintain continuity with minimal power draw — measured under 1 % per day in standby.
Verified Technical Findings
The static analysis of v8.0.00.15 shows a clean, production-grade build. It compiles 13 197 classes and 100 559 methods across two DEX files (13.5 MB). One native library, libDiagMonKey.so, handles diagnostic logging. The code references Android X and Kotlin frameworks, targeting API 35 (Android 15).
The package exports only one UI activity (CMCWrapperActivity) and three network services (NmsService, MdecServiceTiles, PnReAgreementJobService) tied to system permissions. None expose user data.
Should You Keep It Enabled?
If you use multiple Galaxy devices, absolutely. Disabling it breaks instant messaging continuity, notification mirroring, and SmartThings integration. For single-device owners, leaving the toggle off saves a small amount of background power without risk. The app consumes only a few megabytes of storage and negligible network traffic.
Think of it as the connective tissue of Samsung’s ecosystem — invisible until removed. When active, it ensures your Galaxy Tab receives calls, your watch mirrors messages, and your phone knows when another device is ringing.
The Real Takeaway
Most users never notice MDEC until they stumble across its name in a battery report. Yet it’s one of the clearest examples of how modern Android hides complexity behind convenience. The permissions look intimidating because cross-device communication can’t happen without deep access, but the design is deliberate, transparent, and bound by Samsung’s sandbox.
com.samsung.android.mdecservice isn’t bloatware or spyware — it’s infrastructure. It’s what keeps the line open between your phone, your tablet, and your watch, quietly proving that the most useful parts of an ecosystem are the ones you never have to think about.