com.android.captiveportallogin isn’t something you install. You won’t find it in the Play Store, and it doesn’t have an icon. But it runs on nearly every Android phone — quietly — the moment you connect to certain Wi-Fi networks. And when it does appear, it usually means one thing: Android is checking if you’re allowed online.
That’s when the questions start.
What Is com.android.captiveportallogin on Android?
com.android.captiveportallogin is a system component that handles login pages on public Wi-Fi. It activates when Android detects a network that blocks internet access until you agree to terms or sign in — usually at places like hotels, airports, cafés, or schools. This process is called a captive portal, and Android checks for it automatically using a background HTTP probe , often directed at connectivitycheck.gstatic.com.
If that probe is redirected — instead of returning a “204 No Content” — Android launches CaptivePortalLogin. It opens a minimal WebView window to display the network’s login page, independent of your browser or apps. Once you complete the login or the portal clears access, the system closes the window and marks the connection as unrestricted.
The entire process runs under the package name com.android.captiveportallogin. It has no manual launch option, and no role outside this specific Wi-Fi validation check. You’ll only see it in system logs, battery stats, or usage history if the login process fails or is triggered repeatedly.
Is com.android.captiveportallogin Safe or Spyware?
It’s safe.
com.android.captiveportallogin is verified by Play Protect and signed by your device manufacturer or Google. It doesn’t request special permissions, doesn’t run unless triggered by a restricted Wi-Fi network, and has no access to your personal data, location, or background services.
Some users report seeing it in battery usage or system activity logs and assume it’s tracking them. It’s not. If it appears frequently, it usually means the network is forcing repeated authentication — not that the app is acting on its own.
Security scanners may occasionally flag it on rooted devices or custom ROMs, but that’s a false positive. It doesn’t stay open, doesn’t persist, and once the network clears access, it shuts down automatically.
Why com.android.captiveportallogin Keeps Popping Up or Crashing
When CaptivePortalLogin keeps stopping or starts crashing, it usually means the network you’ve connected to isn’t behaving as Android expects. This system process relies on clear signals — either access is granted or blocked. Anything in between causes issues.
One common trigger is a network that redirects the login page inconsistently. Instead of a single step, it might loop between multiple URLs or inject ads and tracking scripts that interfere with Android’s probe. In that case, the login window may keep reopening, stall mid-load, or silently restart in the background.
VPNs and encrypted DNS services often block or mask the connection test Android uses to detect captive portals. When this happens, the system can’t verify whether the network allows internet access, so CaptivePortalLogin assumes it’s still restricted. You may see the login page open and close repeatedly or fail to appear at all.
In some cases, the issue isn’t the network — it’s the WebView component itself. CaptivePortalLogin uses a stripped-down Android System WebView to display the portal, and if that layer is outdated or corrupted, the login screen may fail to load or crash on launch. You won’t always see an error, but the app may leave entries in battery stats or crash logs.
Network timeouts can also force the process to restart. Some public hotspots drop idle connections after a few minutes, requiring you to re-authenticate. Android detects the change and re-launches CaptivePortalLogin automatically, even if you’re not actively using the network.
Occasionally, users notice it listed as using background data, especially on buggy or ad-heavy Wi-Fi networks. This isn’t the app using data on its own — it’s the network’s portal loading scripts or resources during the login flow, which gets attributed to CaptivePortalLogin by the system.
Can You Remove com.android.captiveportallogin?
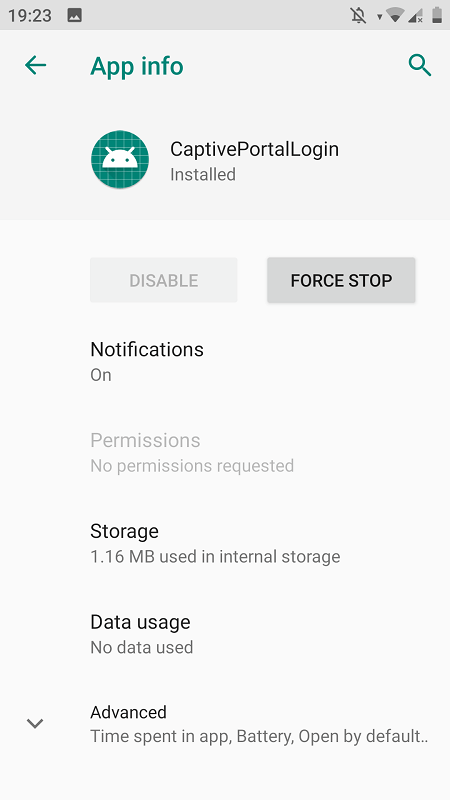
Android doesn’t offer a setting to turn it off. CaptivePortalLogin is part of the core system, and for most users, it stays hidden until triggered. You won’t find an uninstall option, and force stopping it has no effect — the process will relaunch as soon as a captive network is detected.
For advanced users, ADB can disable it, but this blocks the login screen entirely. You’ll still connect to Wi-Fi networks, but those requiring a browser-based login will appear broken — no prompt, no access, no explanation. The connection will fail silently unless handled manually through a browser, which often doesn’t work without system-level detection.
Rooted users can remove the package completely or freeze it using tools like Titanium Backup. Doing so prevents captive portal handling across the entire system. That includes college campuses, buses and trains, fitness clubs, or any public access point that uses redirection. It won’t affect mobile data or private Wi-Fi, but open networks that require terms or authentication will stop functioning as expected.
For users who never connect to public Wi-Fi, disabling it might not cause problems. But for everyone else, removing it means losing the system’s ability to handle access-controlled networks — and that breakage isn’t always obvious.
Final Take
com.android.captiveportallogin doesn’t track you, and it doesn’t run without a reason. It exists to solve a specific network problem — getting you past Wi-Fi walls that block internet access. Most of the time, it stays invisible. When it doesn’t, it’s either the network that’s broken, or something else is getting in the way.
Knowing how it works means you don’t have to guess. You can ignore it, disable it, or leave it alone — but now you know exactly why it’s there.
More Android Packages We’ve Covered:

