On many Android phones, Facebook doesn’t behave like an ordinary app. It runs when you haven’t launched it, stays active after resets, and appears in logs under a name you didn’t search for: com.facebook.katana. That package isn’t suspicious. It’s the system name for the Facebook app. But when it’s embedded into firmware or pre-installed, it plays by different rules, ones that let it trigger without you doing anything.
What “com.facebook.katana” Actually Represents
Every Android app has a permanent system identifier called a package name. This name never changes regardless of updates, UI changes, or rebranding. For Facebook, that package is com.facebook.katana. It’s the same on every phone and version. If you check crash logs, battery usage, or system diagnostics, this is what Android will use.
This package doesn’t operate the same on every device. If you installed Facebook manually, it’s treated like any user app — uninstallable, sandboxed, and removable. But if your phone shipped with it preloaded, that version often lives in /system/priv-app/ or /vendor/. That gives it persistent access to protected resources and prevents full removal without root, which this guide avoids entirely.
Preinstalled Facebook Apps Trigger Differently
Apps stored in privileged partitions aren’t limited to user actions. They can respond to system broadcasts like BOOT_COMPLETED, CONNECTIVITY_CHANGE, PACKAGE_ADDED, and others — all without being explicitly opened. These aren’t malicious triggers. They’re allowed behaviors for apps granted elevated install permissions.
If Messenger or Instagram is installed and uses Facebook Login, parts of the katana package may activate silently to sync sessions. This is expected behavior, not misuse. It’s the result of shared service registration inside the Android AccountManager and AppOps layers which treat com.facebook.katana as an authentication provider, not just an app icon.
What’s Inside com.facebook.katana
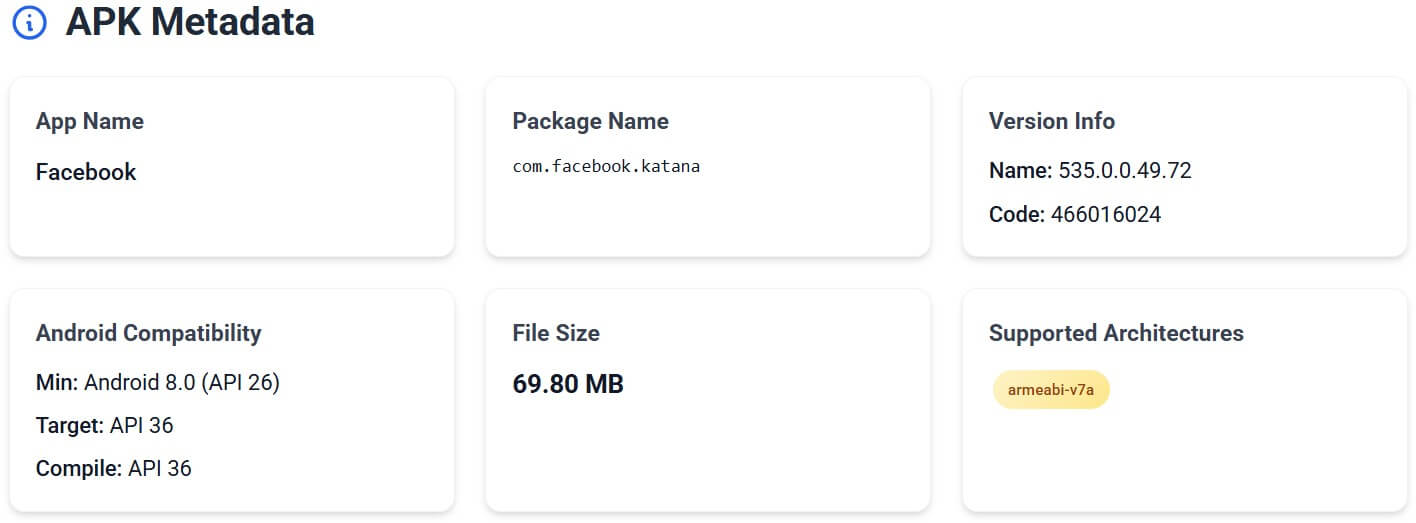
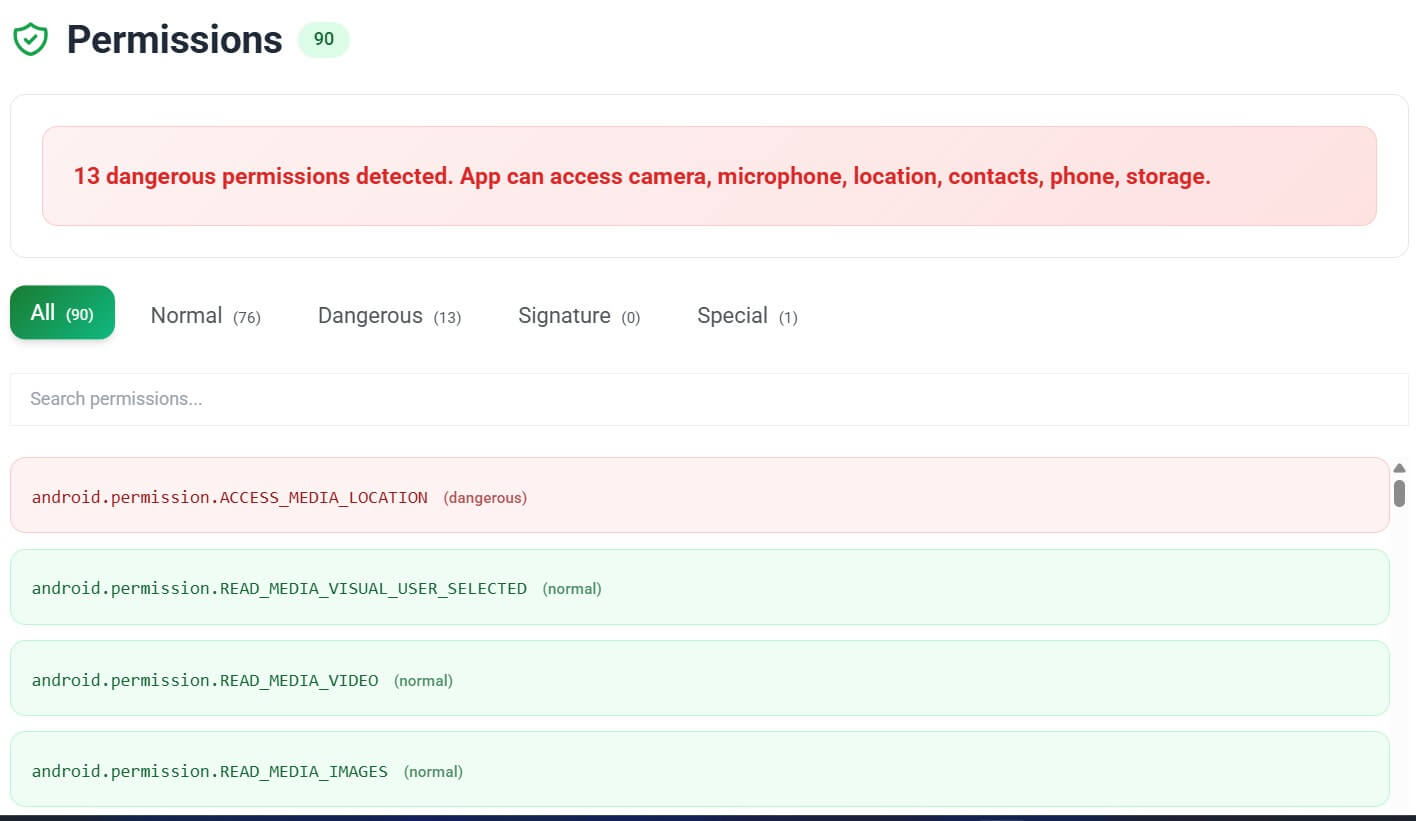
Facebook’s APK is large because it’s modular. Based on a local static analysis using our APK Analyzer tool, APKMirror version 535.0.0.49.72 (as distributed on many 2025 builds) requests over 90 permissions, with 13 classified as dangerous under Android’s protection levels. These include access to the camera, contacts, location, sensors, and clipboard, but no longer call logs, which are restricted by modern Android privacy policies.
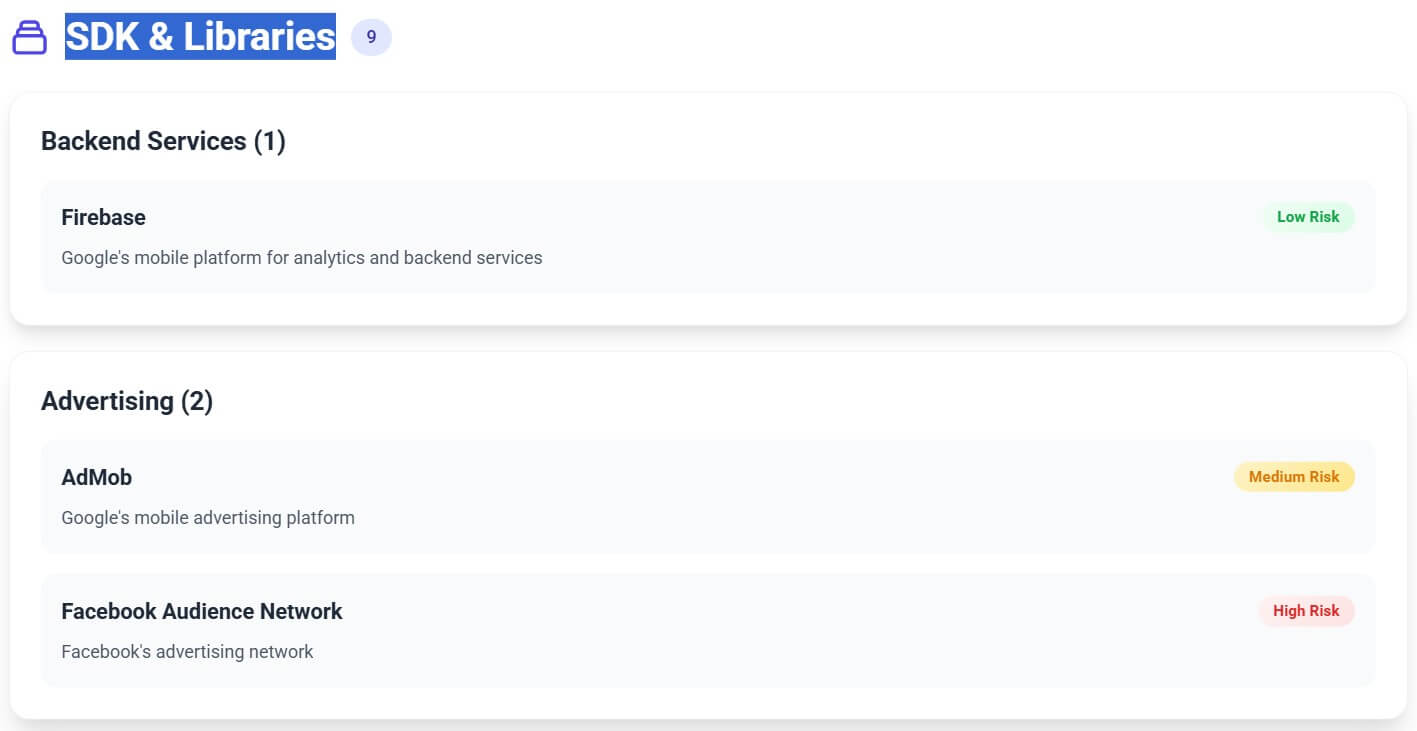
The app integrates several SDKs, such as:
- Firebase Crashlytics for fault reporting
- Meta Audience Network for ad serving
- App Events for internal telemetry
- Shared modules for Messenger login and Instagram cross-posting

It also exposes numerous exported components — including services, broadcast receivers, and content providers — not only for internal use, but also for external intent calls from other apps on the device. While Play Protect scans and signs this APK as valid, its reach across the OS is broader than most user-facing apps.
The package does not hide its identity. Its signature matches Meta’s production keys, and its manifest lists intent filters for numerous app-linking actions. Its behavior aligns with a service-oriented integration, not a malicious agent.
What This Means for Performance and Privacy
The Facebook app stays ready through Android’s JobScheduler and WorkManager, which queue background jobs for sync, analytics, and account refresh. These run occasionally to keep linked services aligned but shouldn’t stay active for long.
Since Android 12, background location access is restricted to foreground use unless you explicitly allow “All the time.” Even so, the app can hold cached login tokens for account APIs. On some firmware versions, it also links into system features such as Digital Wellbeing, Family Link, or Samsung’s Device Care — which may still report brief activity or wake cycles even when the app itself isn’t open.
How to Stop Facebook Crashes or Battery Drain Safely
Suppose the Facebook app starts crashing or draining battery unexpectedly. In that case, it’s often due to background services getting out of sync after Android version upgrade, permission resets, or mismatched versions of other Meta apps.
These inconsistencies can leave certain components, such as cached login tokens or stale receivers, actively consuming memory and resources. The steps below show how to reset these safely without root or ADB.
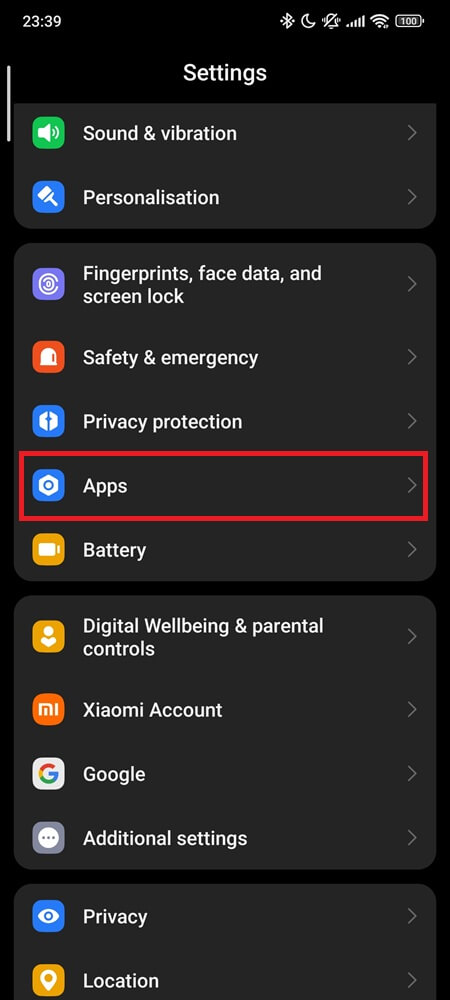
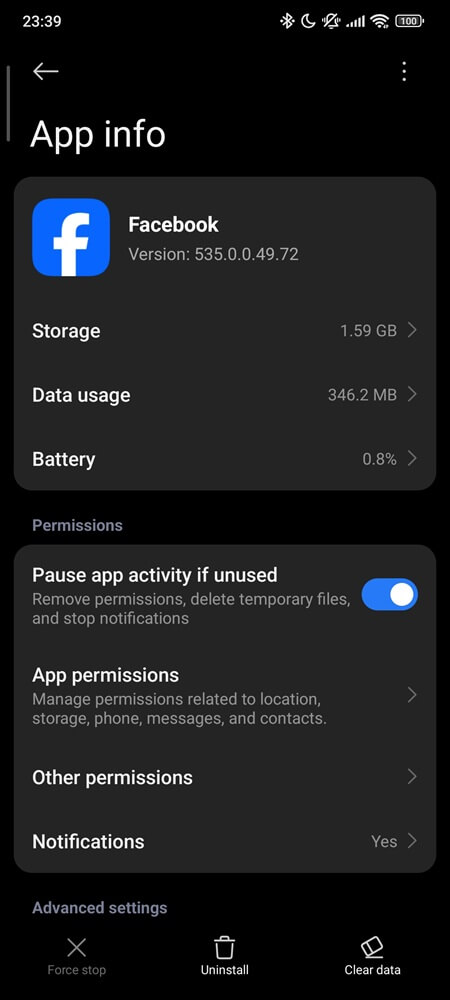
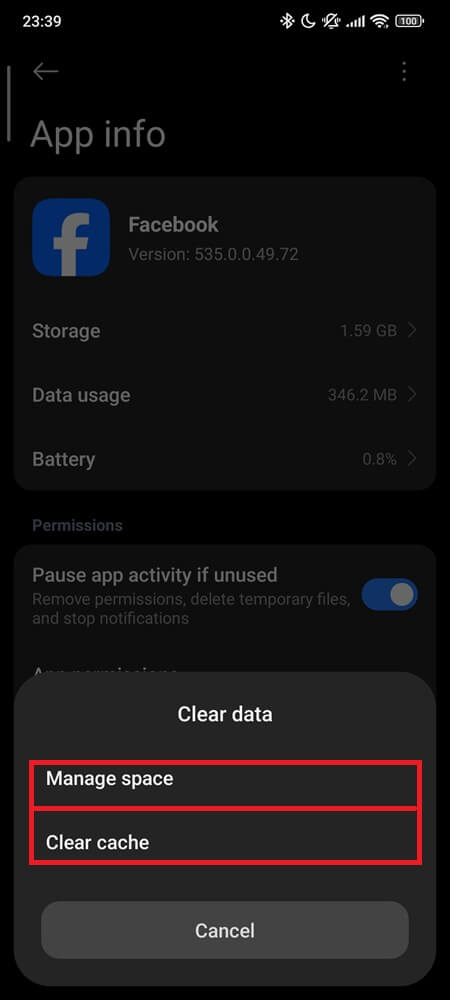
1. Clear Facebook cache and storage
→ Settings → Apps → Facebook → Storage
→ Clear Cache, then Clear Storage (or tap Manage Space depending on your Android version)
2. Uninstall updates (if app is preinstalled)
→ Settings → Apps → Facebook
→ Tap the three-dot menu > Uninstall Updates
→ Reverts to factory-stable version that’s less error-prone
3. Update Messenger and Instagram
→ Open Play Store and update both apps fully
→ Prevent shared service mismatches that cause crashes
4. Reboot after cleanup
→ Ensures service jobs, cached state, and receivers are reset
5. Disable the app if you don’t use Facebook
→ Settings → Apps → Facebook → Disable
→ This stops background jobs, hides the icon, blocks receivers, and freezes internal triggers
If the disable or uninstall updates option is missing, your device policy or carrier ROM may restrict it. In that case, storage and permission revocation still helps reduce activation. You do not need to attempt root, ADB, or debug shell methods — they’re unnecessary and potentially dangerous.
Uninstall Behavior Depends on How It Was Installed
There is no one-size-fits-all method. Facebook behaves differently depending on its install source:
1. If you installed it from Play Store:
→ You can fully uninstall it like any other app (Go to Play Store → Search Facebook → Tap Uninstall)
→ Deletion removes both app and all package data
2. If it was preloaded (system app):
→ You cannot uninstall it without root
→ You can only uninstall updates or disable it
3. If using a third-party tool like System App Remover:
→ Avoid it unless you know your firmware allows safe removal
→ Some removers break internal service chains, especially on Samsung’s One UI, MIUI, or HyperOS
4. Do not use ADB shell commands
→ pm uninstall --user 0 com.facebook.katana might appear safe but can break dependencies with Messenger, login frameworks, or other apps that use shared user IDs if its done incorrectly
→ No longer recommended for public guides unless verified per device
Why It Still Appears After Disabling
Disabling a package does not erase its history. Android usage data is not instantly wiped — especially for apps that previously handled system events. Even if frozen, the system may still log idle receiver registrations, usage stats, or account sync triggers.
In most cases, usage logs refresh automatically within a few days of inactivity, depending on the device and Android version. If you see com.facebook.katana listed in battery usage or activity monitor after disabling, wait. It does not mean the app is running — it means the OS hasn’t cleared the record yet. These records are stored in usage-history.xml, battery-historian, and occasionally via AppOps logs.
If it reappears after a full cooldown, it’s likely being triggered by another Meta app. Logging out of Instagram and Messenger, revoking Facebook’s AccountManager access, and rebooting the device will fully isolate it. After that, logs stop.
Final Note
com.facebook.katana is not malware. It’s not spyware. But it is one of the most integrated packages in Android, especially when pre-installed. You don’t need to panic over its name in a log, but you also don’t need to let it stay active if you don’t use it.
Disabling it doesn’t break your phone. It doesn’t cause app crashes or erase other apps. And when done correctly with updates removed, services cleared, and linked accounts signed out, it stays silent.