You tap into your system logs or check battery usage and find something called Android System SafetyCore. No app icon. No settings. No explanation. Just a background service with a name that sounds official but tells you nothing.
So, why is this thing even on your phone—and what happens if you try to remove it?
What Android System SafetyCore Is
SafetyCore is a modular system component created by Google under its Project Mainline initiative. It runs under the package name com.google.android.safetycore, and it’s not meant to be seen, opened, or controlled by the user.
Its job is narrow but sensitive: provide on-device image analysis when called by apps like Google Messages. That includes detecting NSFW content before it’s displayed to the user. It’s an invisible backend utility designed to respond only when a supported app explicitly triggers it.
You’ll only find it on devices that run Google Mobile Services (GMS). That means de-Googled phones, AOSP forks, and ROMs like GrapheneOS or LineageOS (without GApps) won’t have it installed.
Why It Was Installed Without Asking
SafetyCore doesn’t come through the Play Store. It’s shipped silently through Play System Updates, which use APEX containers that operate deeper than app layers.
You don’t get notified. You don’t see a changelog. You don’t approve the install. That’s by design.
This isn’t a bug. It’s Google’s solution to fragmented update chains across Android devices. By bypassing manufacturers and carriers, Google ensures certain services—like SafetyCore—are always up to date, regardless of your phone brand or Android version.
That’s how you ended up with a hidden scanner in your system settings, even if you’ve never used the app that relies on it.
What SafetyCore Actually Does
SafetyCore isn’t running 24/7. It doesn’t crawl your gallery. It doesn’t pre-scan photos. It only activates when a compatible app makes a request.
Take Google Messages as the key example. If a new MMS image comes in, the app can hand that file to SafetyCore. The module processes it locally, flags it if necessary (e.g., “contains nudity”), and sends back a binary result.
The app then decides how to respond. Usually, that means blurring the image behind a “Sensitive Content” warning. You can still view it, but the warning acts as a visual buffer.
No scanning happens in the background. No other apps can access it without permission. If no one calls it, it does nothing.
Is SafetyCore Uploading or Syncing Anything?
No. That’s one of the few certainties about it.
SafetyCore doesn’t have internet access. It doesn’t sync. It doesn’t ping Google’s servers with your content or scan results. It operates using on-device machine learning models—the same kind used for spam filtering or keyboard suggestions.
No telemetry, no metadata collection, no cloud integration. Whether you’re online or not, SafetyCore’s job ends at local analysis. Even root-level traffic sniffers won’t catch it reaching out.
If this module was leaking anything, it would’ve been exposed already.
Why People Still Don’t Trust It
The issue isn’t what SafetyCore does—it’s how it was delivered.
- No onboarding
- No controls
- No documentation
- No transparency
It appears out of nowhere. And it handles one of the most sensitive types of data—images that may be private, explicit, or emotionally charged.
Even if it never connects to the internet, the lack of user agency creates distrust. Android users expect power, not mystery.
Privacy is about perception, control, and consent. The system’s developer skipped all three.
Can You Remove Android System SafetyCore?
It depends on how your phone received it. Google doesn’t officially recommend removing or disabling SafetyCore, since it plays a role in content filtering and system stability. But if it was installed as a regular system app, you might see a “Disable” or “Uninstall” option in the Play Store or App Info menu.
If it’s bundled as an APEX module, removal gets more complicated. These are treated like system libraries. Most phones don’t expose them directly—and even ADB has limited access.
Still, here’s what might work:
ADB (non-root)
Modifying SafetyCore can cause system instability or data loss. Only attempt if you’re an advanced user and always back up your device first. Then, start by enabling USB debugging. Tap Build number in About phone until Developer options unlock, then flip on USB debugging.
Connect your phone to a computer with ADB installed. When the prompt shows up on your phone, approve USB debugging access.
In your terminal, type adb devices — your phone should show up. If not, fix your USB connection or drivers.
Then run:adb shell pm uninstall --user 0 com.google.android.safetycore
If it says Success, it’s gone — at least for your user profile. If you get Failure [not installed for 0], that means it’s locked in as an APEX system module and can’t be touched this way.
No reboot needed. No data lost. And if you ever want it back, just run:adb shell cmd package install-existing com.google.android.safetycore
Play Store Uninstall
Some phones let you manage SafetyCore like a regular app. Go to the Play Store, search for Android System SafetyCore, and tap the gear icon or three-dot menu.
If you’re lucky — and your device isn’t locking it down — you’ll see an Uninstall option. This happens more often on Samsung, Motorola, and some Xiaomi models where the module wasn’t bundled as APEX.
But if you don’t see anything except “Installed,” it means the system blocked user access. Nothing to do there — move on.
Root users
If you’ve rooted your phone, you’ve got more power—and that means more ways to kill SafetyCore for good.
Your two best tools:
- Universal Android Debloater (UAD): This lets you freeze or uninstall system components with zero guesswork. Launch UAD on your PC, connect your phone via USB, and look for com.google.android.safetycore in the list. If it shows up, you can safely remove it.
- Magisk Module (Advanced): Use a Magisk module like Debloat or App Manager to isolate and block SafetyCore at boot or to hide it entirely from system logs and app scanners.
If freezing doesn’t work—or the module reappears—try combining root tools with ADB uninstall to double-block the package across both layers. Just make sure your Magisk setup is stable first. A broken SafetyCore install + root conflict = instant system UI crash risk.
Note: Even if successful, Play System Updates can reinstall SafetyCore later. You’d need to blacklist the package or block update propagation to keep it off permanently.
What If It Crashes or Drains Battery?
For most users, SafetyCore never crashes. But on buggy firmware, you may get: “Android System SafetyCore keeps stopping” Or a battery report showing unexpected activity.
That usually means:
- A broken or corrupted SafetyCore update
- Incompatibility with another Google service
- Background interference from a task manager
- Device modification (root, custom ROM) causing permissions conflict
If Android System SafetyCore keeps crashing, try this fix:
1. Reset Google Messages Data
Messages is the top trigger for SafetyCore. If it’s storing a bad image or preview, the whole system can break.
Go to Settings > Apps > Messages > Storage > Clear data (steps may vary slightly depending on your phone model and Android version).
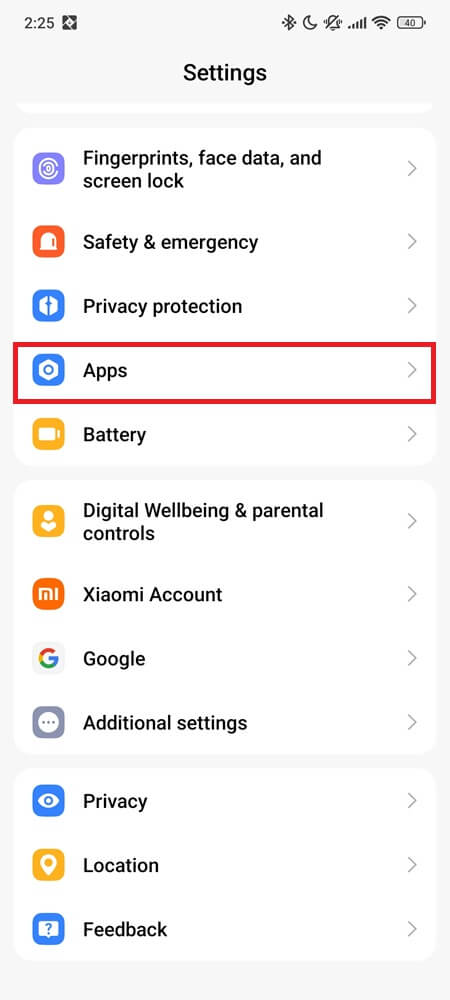
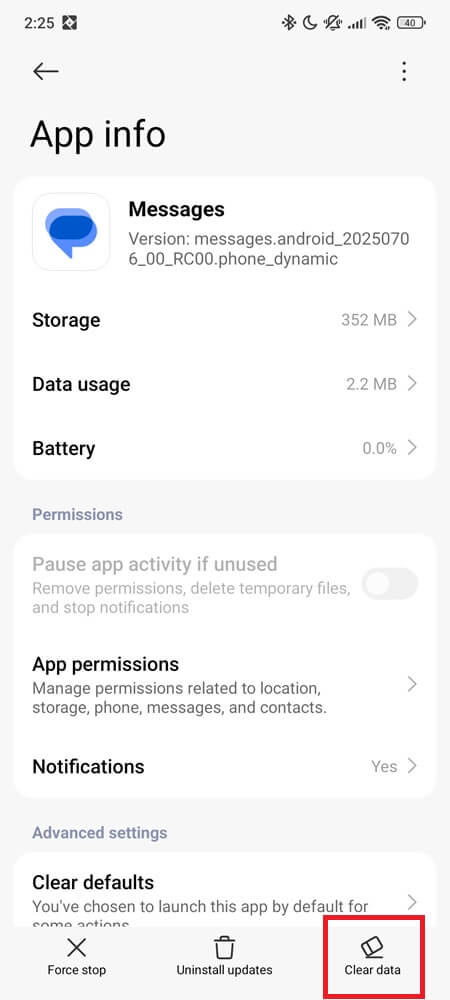
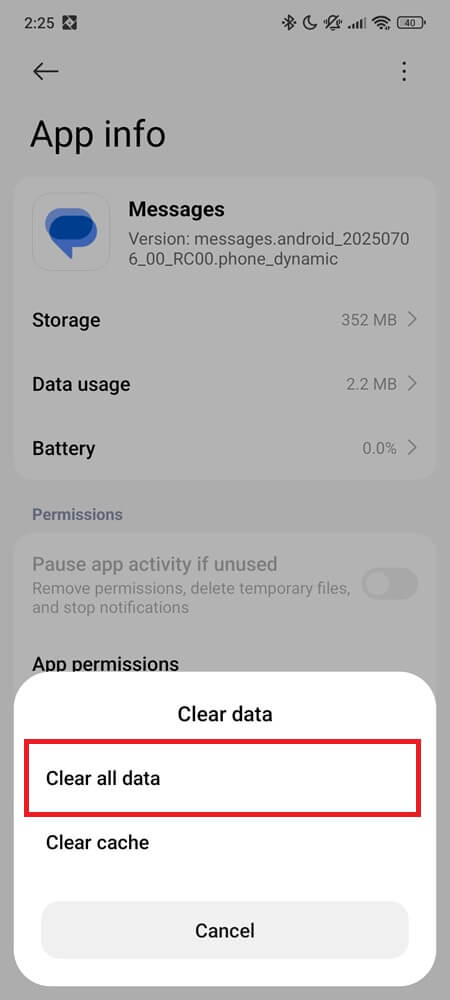
Then open Messages again and test with a fresh MMS.
2. Update Play System Modules
Corrupted Play system modules are the #1 crash source. Updating them will often reinstall or patch SafetyCore silently.
Go to Settings > Security & privacy (or Fingerprints, face data, and screen lock) > Updates > Google Play system update.
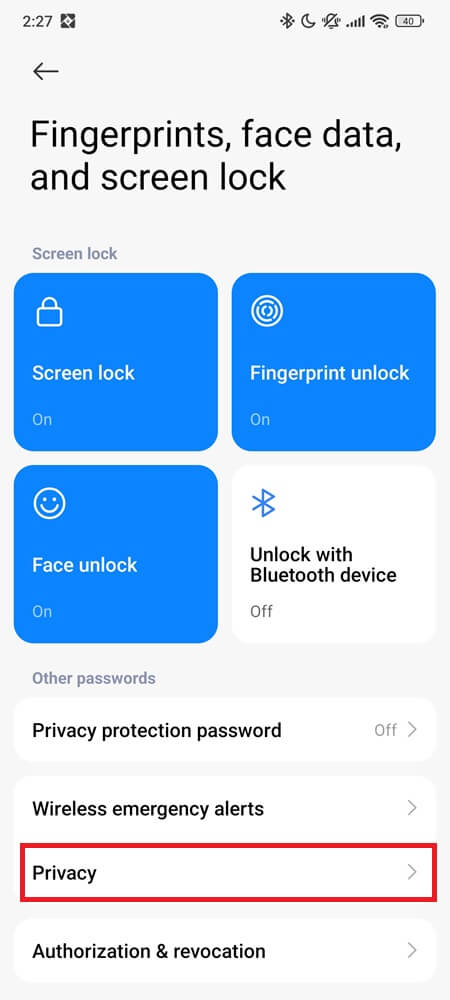
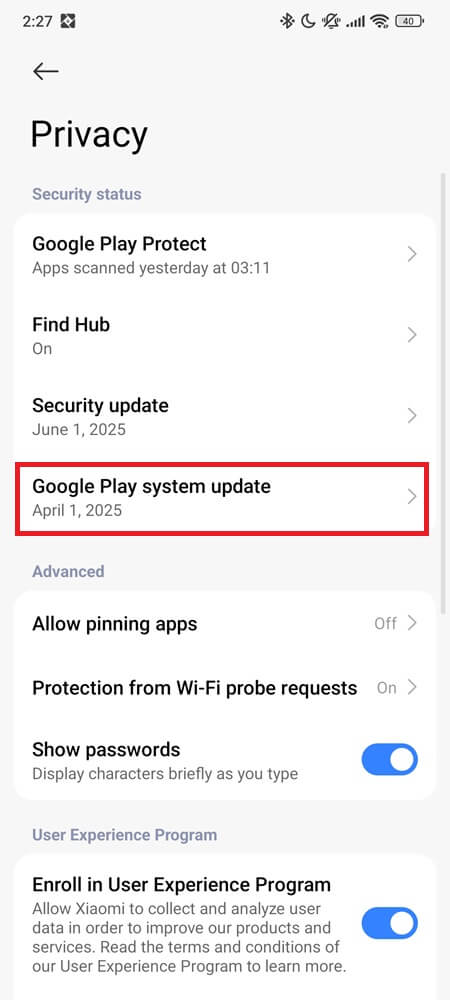
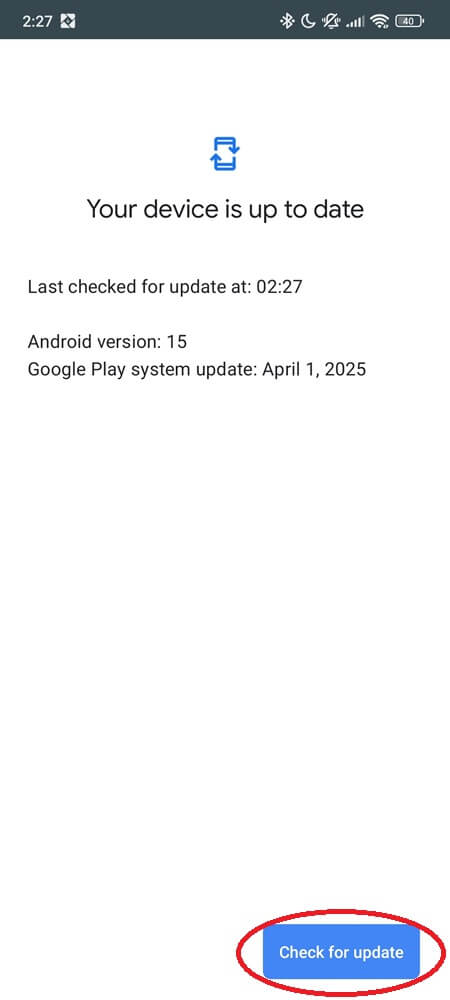
Install anything available—even if it says “Up to date,” tap it and check again. Then reboot.
3. Check for Software Updates
If your firmware is outdated or buggy, system-level modules like SafetyCore may crash randomly.
Go to Settings > Software update > Download and install.
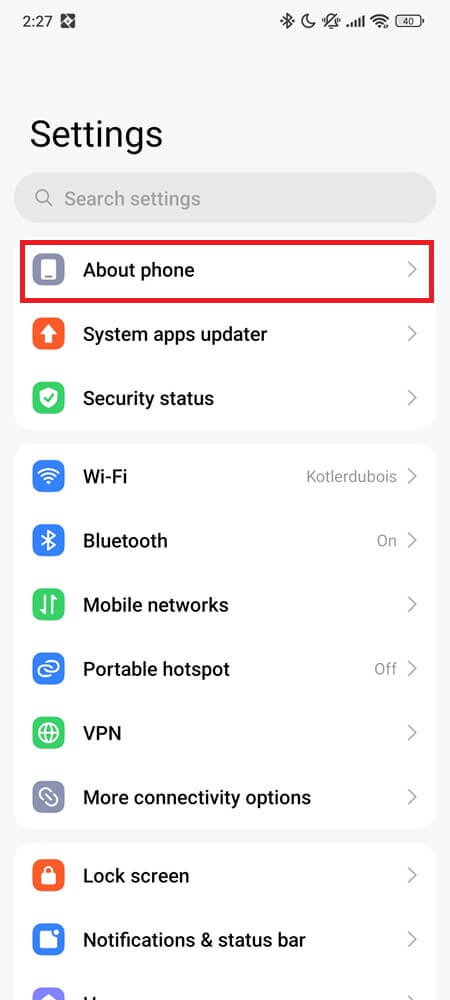

Let it finish fully—even background security patches can stop the issue.
Don’t bother with “clear cache”—this isn’t a cache-based app.
Why This Matters for Android’s Direction
SafetyCore is a signal.
Google is moving Android deeper into modular territory. More APEX modules. More invisible services. Less user control. That’s not just a trend—it’s a roadmap.
In the past, system-level updates came with a version number and a changelog. Today, entire modules are being installed, updated, and activated without a single user prompt.
The feature may be harmless. The delivery method isn’t.
We’re not debating surveillance here. We’re debating transparency. And once that disappears, even privacy-friendly services start to feel like overreach.
Related articles:

